Azure Architecture Scenario: Protect an Azure App Service with a Cloud Hosted WAF (DNS Based)
Project Overview
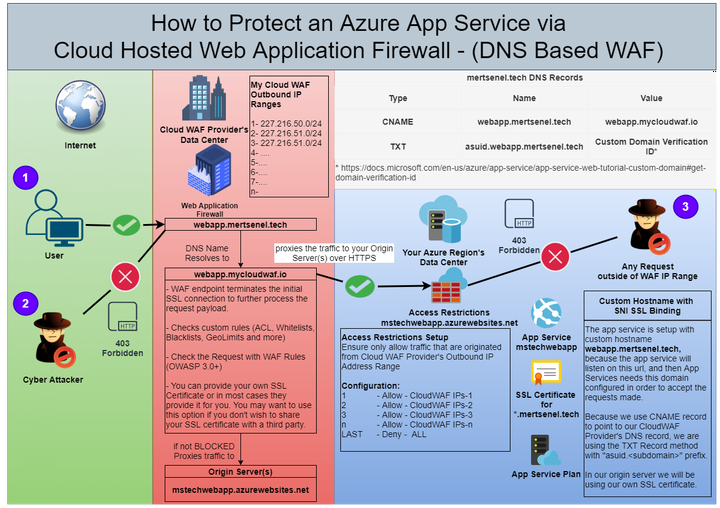
This is a whiteboard sample architecture that shows how to secure access to an Azure App Service hosted public and client facing application/api behind a WAF that is managed and hosted outside.
This particular example was based on Incapsula/Imperva Web Application Firewall and their implementation but it would be very similar for most of the DNS based WAF providers.
As the main requirements doesn’t change:
First, you need to proxy(pass) the traffic coming to your application via your WAF provider’s infrastructure, that way you make sure that the traffic is inspected by the WAF and rules you defined are applied to it.
Second, you need to make sure your WAF can reach your origin servers
and Third, make sure you are limiting access to your App Service only from the Web Application Firewall’s Outbound IP ranges.
This flow would be similar for a Virtual Network hosted applications as well such, as Kubernetes Clusters, Virtual Machines, App Service Environment in short anything where you can apply a Network Security Group. If this is the case one can just apply the same whitelisting logic of the outbound IP ranges of the WAF provider, to the inbound rules of the Network Security group.
The reason I’ve made this sample with the regular Public App Service is that, for someone who doesn’t knows it’s full feature set, they might consider it an hosting solution that can’t be secured or locked down. They might say, it’s public hence it’s not secure think they need to either opt-out from using App Services or forced to upgrade to an App Service Environment.
If you use another provider like Cloudflare where they also forces you do use them as your DNS provider, in this case the CNAME record is automatically handled for you, you just need to make sure you turn on the “orange” cloudflare proxy mode on for your particular subdomain and limit access to your App Service to only Cloudflare’s outbound IP ranges. I had setup something very similar in the past with Cloudflare WAF and with Azure VM and Load Balancer.
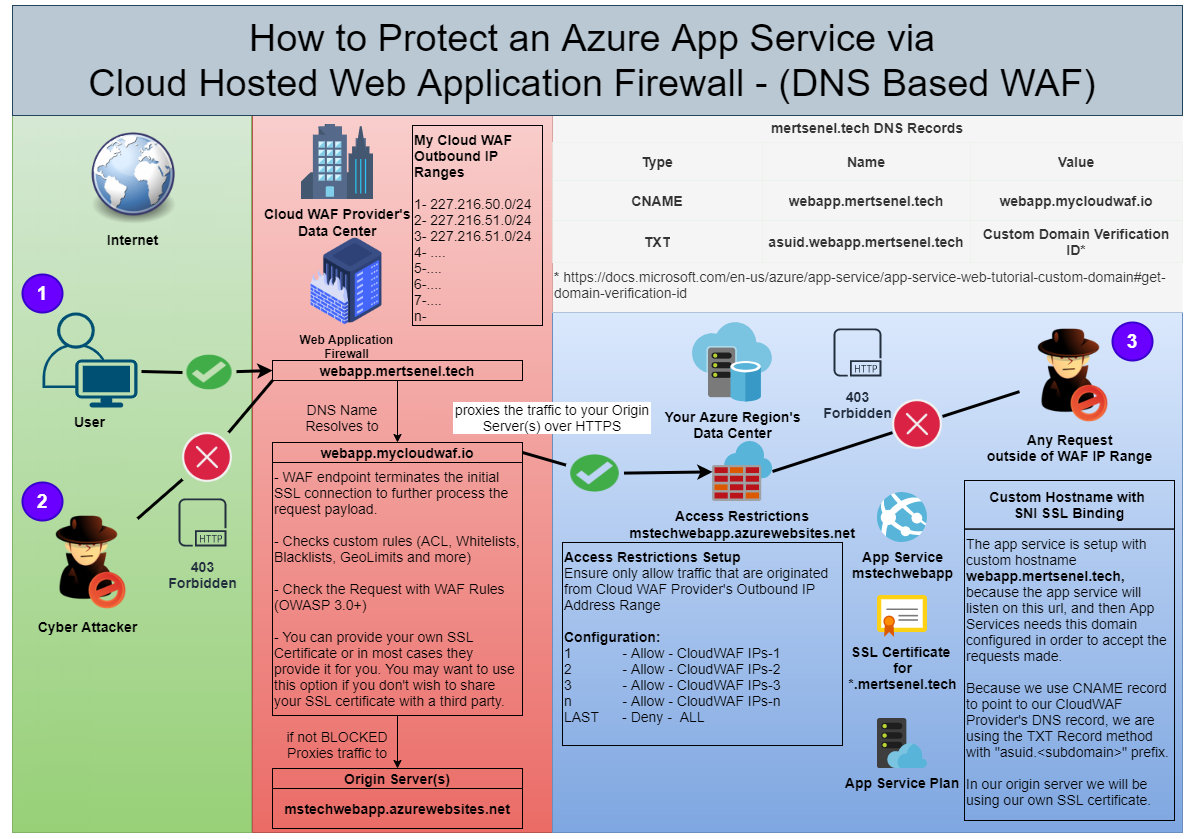
Diagram Details
1- Normal traffic from the users of our application. Their traffic will be processed by Web Application Firewall’s engine and expected to be allowed.
2- Malicious Attacks made to our application will be picked up by the WAF rules processing and blocked.
3- All Access to the App Service outside of the Cloud WAF Provider’s Outbound IP range is blocked by the App Service Access Restrictions.